Continuous Controls Monitoring – Automated GRC Technology
Move beyond legacy approaches to governance, risk, and compliance (GRC) with our auto-scaling, hyper-connected, and ultra-secure platform that deploys anywhere (on-premises, cloud, or air-gapped networks) in minutes.
Trusted by the most effortlessly secure and compliant organizations on the planet
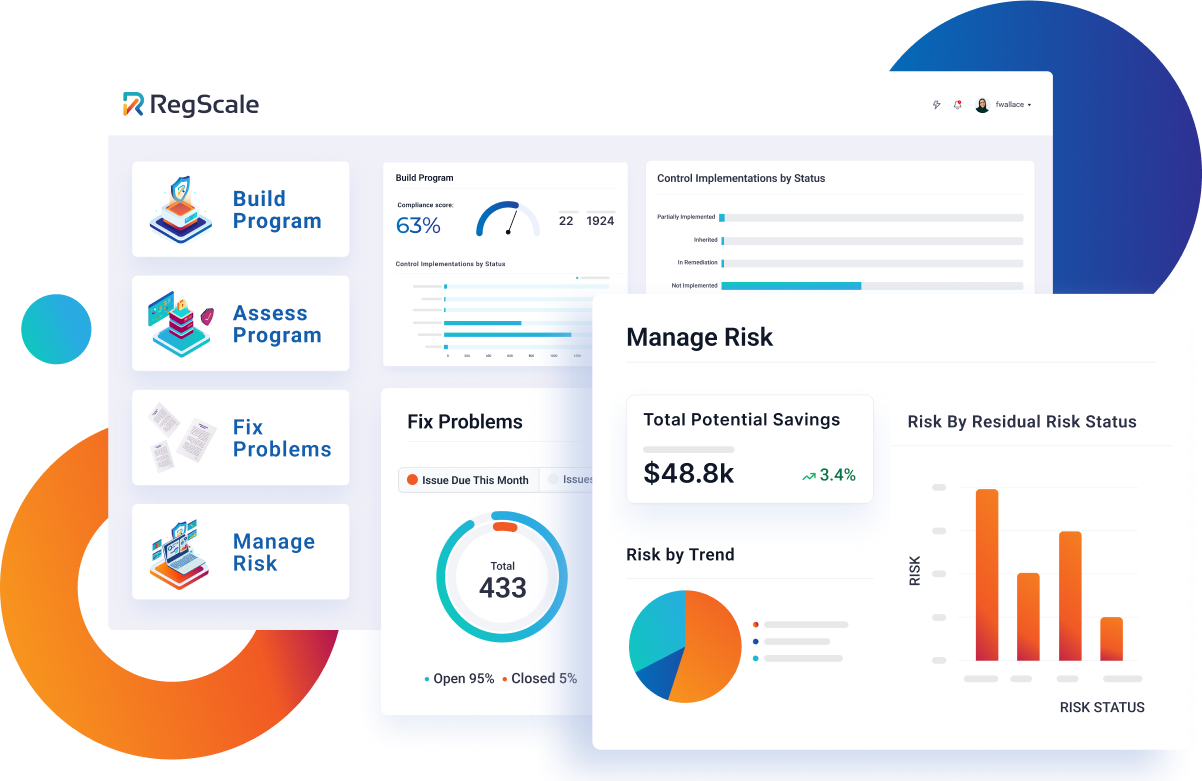
The power of RegScale CCM
Unlocking extreme automation to save time and money
With our industry leading AI, seamless integrations, self-updating paperwork in Microsoft Office, and compliance-as-code architecture, RegScale has leveraged our background in lean value stream mapping to pull cost, time, and risk out of every phase of a control’s lifecycle.
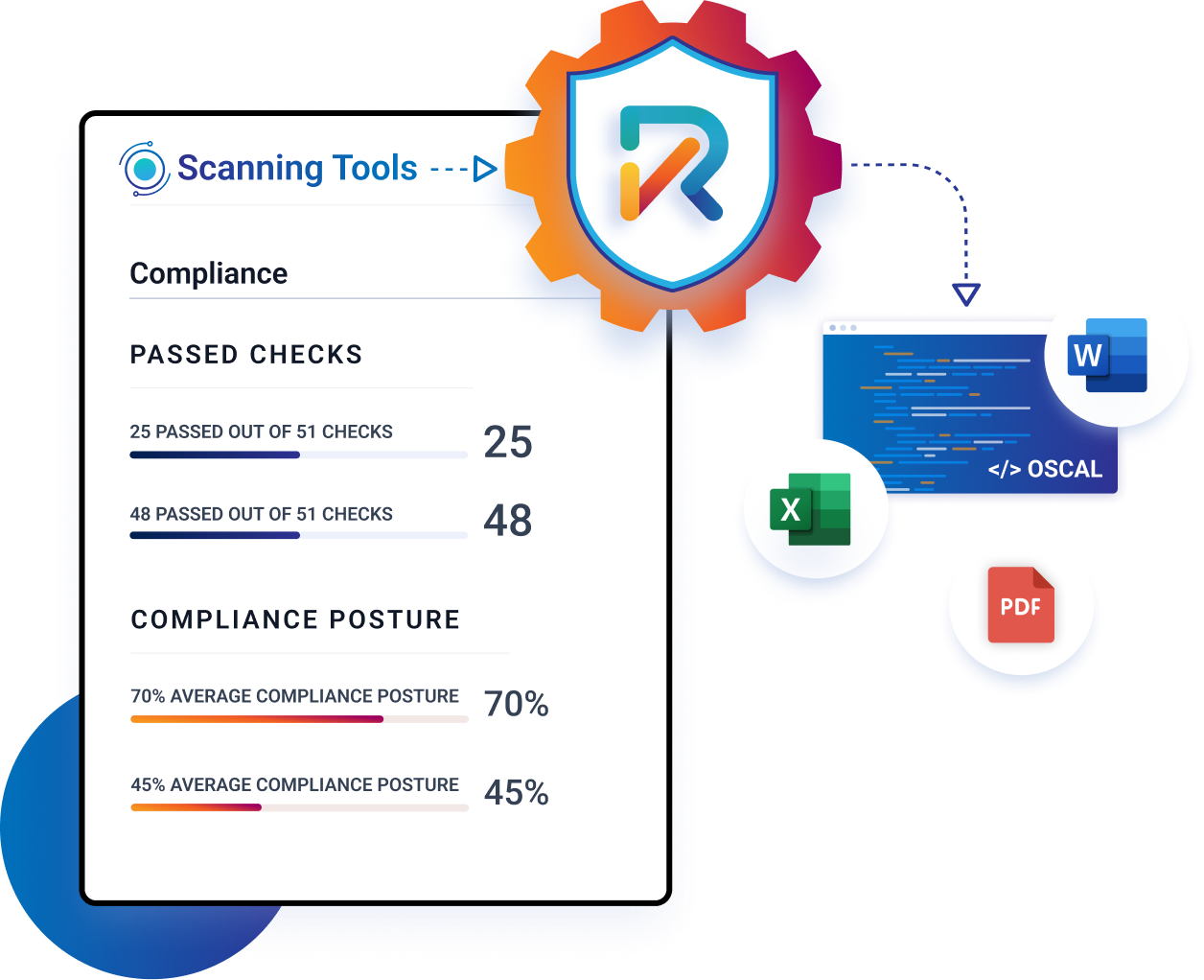
Unleashing Extreme Compliance Automation to Slash Workload
Manual copy-and-paste exercises are soul-crushing endeavors in the risk and compliance arena. Use our plug-and-play automation platform to streamline your workflows and self-generate compliance artifacts in Word and Excel on demand. Your employees will thank you for it!
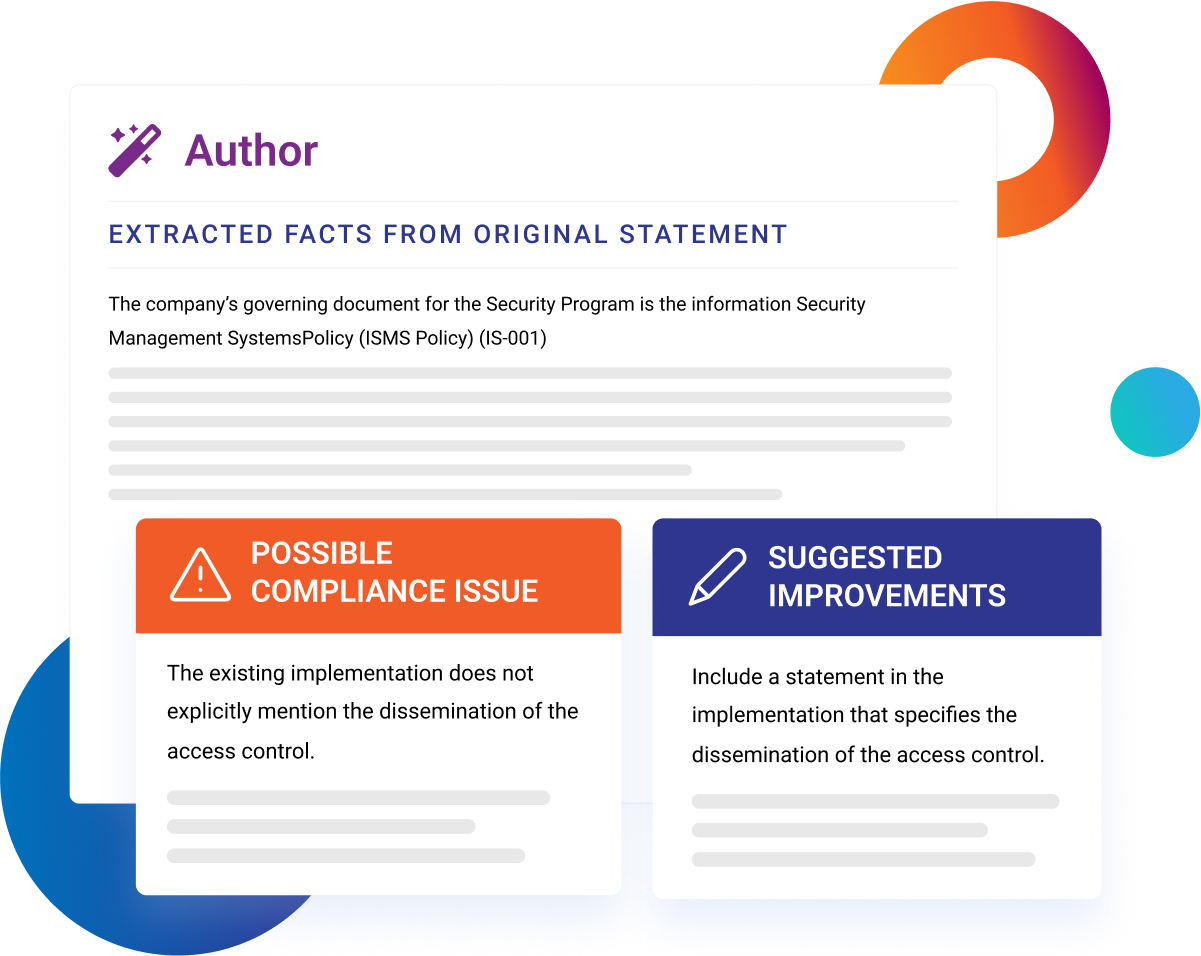
Putting AI to Work Everywhere to Simplify Compliance
The whole industry exists to provide paperwork nobody wants to read, and nobody wants to write. Use our AI to write your controls, conduct your audits, and tell you what is important. Our AI gives you massive amounts of time back so you can focus on more important things.
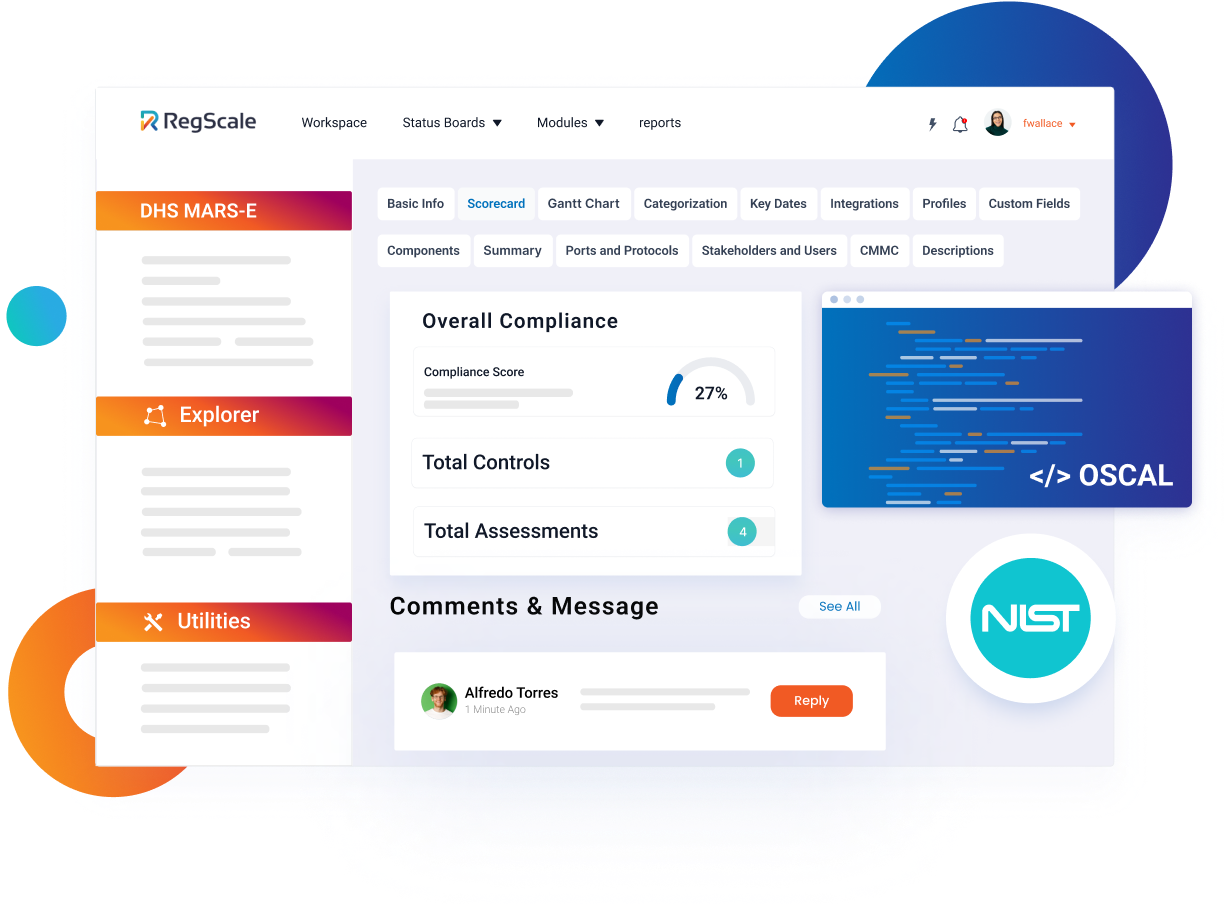
Compliance-As-Code Streamlines Compliance
Built on the NIST OSCAL standard to generate machine readable documentation for your compliance and certification processes. Futureproof your FedRAMP program, build more precise AI models to train on your data, and build a foundation for automation of security and compliance checks.
Supporting Dozens of Frameworks and Catalogs
RegScale helps you navigate the “Cyber Oprah” effect where every regulator has their own framework. We provide out of the box support for over 60 frameworks and partner with Regulatory Change Management platforms for control mapping and content updates.
Built for Security and Trust
RegScale understands the sensitivity of your risk and compliance data, and we built our platform based on a modern Zero Trust architecture that is hardened beyond FedRAMP High to meet the most stringent US military standards.
Seamless Integrations Unite Your Legacy Systems
The RegScale Automation Platform seamlessly integrates with 40+ industry leading tools for vulnerability scanners, ITIL ticketing systems, and hyper-scaler cloud security platforms to allow your tools to self-assess your technical controls and log issues in real-time.

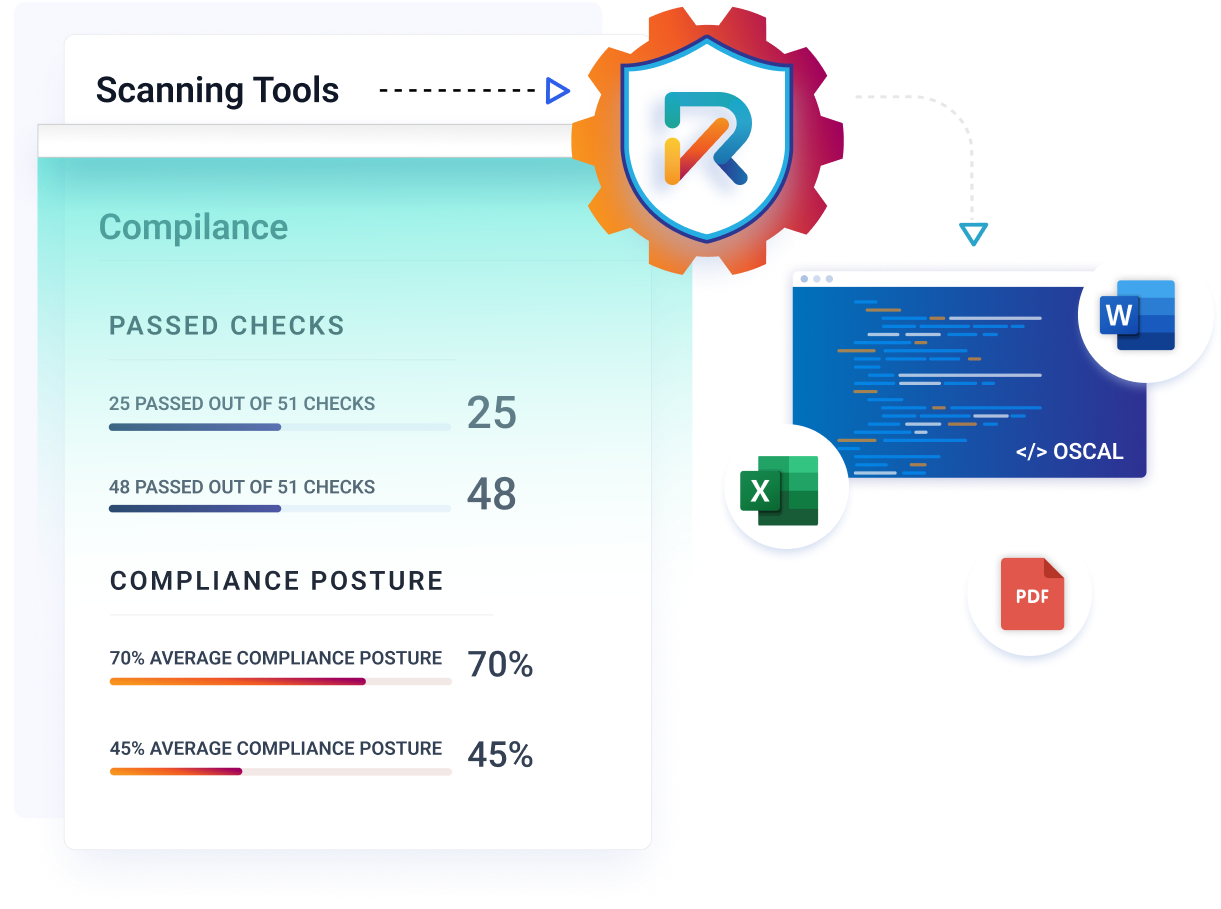
Office Automation Delivers Self-Updating Documents
RegScale supports self-updating paperwork with the ability to auto-generate the Microsoft Word and Excel documents in the exact format expected by your regulators, Board of Directors, or other stakeholders.
Seamless Support for APIs and Graph
In the modern API economy, customers expect that systems interoperate seamlessly. RegScale supports this expectation with 1,300+ APIs and a GraphQL (build your own API) architecture that allows for direct data exchange between systems.


Deploy Everywhere You Choose
No matter your deployment option, RegScale believes in giving customers choice and maximum flexibility. RegScale offers a secure Software as a Service (SaaS) option in the cloud, on-premises deployments, and even hosting within classified or air-gapped networks.
Growing Platform
(RegScale community edition)
(Standards & Frameworks )
(Enables extreme automation)
Ready to fast track your compliance? Let us show you how it’s done
Hey, we know reading can only get you so far. That’s why we’d like to give you a quick, live walk-through of RegScale, to show you exactly what we can do for your organization.












