RegScale + Wiz: Reducing Risk Through Better Vulnerability Management

Software vulnerabilities are an unavoidable fact of software development. They’re also highly labor-intensive. There’s the process of identifying, tracking, prioritizing, and remediating vulnerabilities, and then there’s making sure your team has properly documented, logged, and monitored them.
Even then, uncertainty remains. How can you really make sure you have everything covered? How do you identify all the gaps in your compliance posture, and what assets are most at risk? You need to integrate, log, and monitor different inputs from various tools, as well as automatically map any issue to its relevant category within the framework.
Maintaining the compliance documentation on so many vulnerabilities is even more challenging. Taken all together, you’re looking at a very resource intensive, time-consuming, and error-prone process.
This is where the Wiz and RegScale joint solution steps in. The integration between RegScale and Wiz provides intelligent vulnerability workflows to cut through the noise and focus on the issues that really matter in managing risk.
How Wiz Works Its Magic
Wiz brings a comprehensive approach to cloud security by continuously analyzing multiple risk factors across cloud workloads — from configurations and vulnerabilities to sensitive data exposures and secrets. From there, Wiz identifies the most critical security issues facing an organization and determines which ones pose the greatest threat of data breaches. This enables the platform to automatically prioritize the most significant risks across a company’s cloud environment.
The RegScale-Wiz integration begins with Wiz finding a vulnerability during a scan, which can be a post-deployment scan or a scan during code commit and promotion. The scan result is passed to RegScale, which matches that asset and Common Vulnerabilities and Exposures (CVE) to a vulnerability. This allows RegScale to identify the specific control and framework that is matched to the asset or assets where the vulnerability was found.
Identify and Eliminate Vulnerabilities Faster
Once RegScale has the scan results, and vulnerabilities and assets have been identified and matched, RegScale creates a ticket or issue and a POAM. RegScale then updates the compliance documentation for the asset and the System Security Plan (SSP) the vulnerable asset is attached to.
RegScale’s advanced automation can create one or more tickets in multiple platforms based on numerous contextual indicators — including who the specific responder is, what scanner found the vulnerability, the type of vulnerability, whether the vulnerability is in production or in development, and who is responsible for the asset. For example, a vulnerability found during code promotion early in the development cycle could be routed to the DevOps team, whereas a vulnerability found post-deployment could be routed not only to DevOps but also to AppSec, to the SOC and to IT.
With RegScale’s industry-leading integrations, tickets can be opened in Jira, ServiceNow, and a host of other ITIL platforms. Those tickets will continue to be tracked by RegScale’s platform to capture updates in real-time.
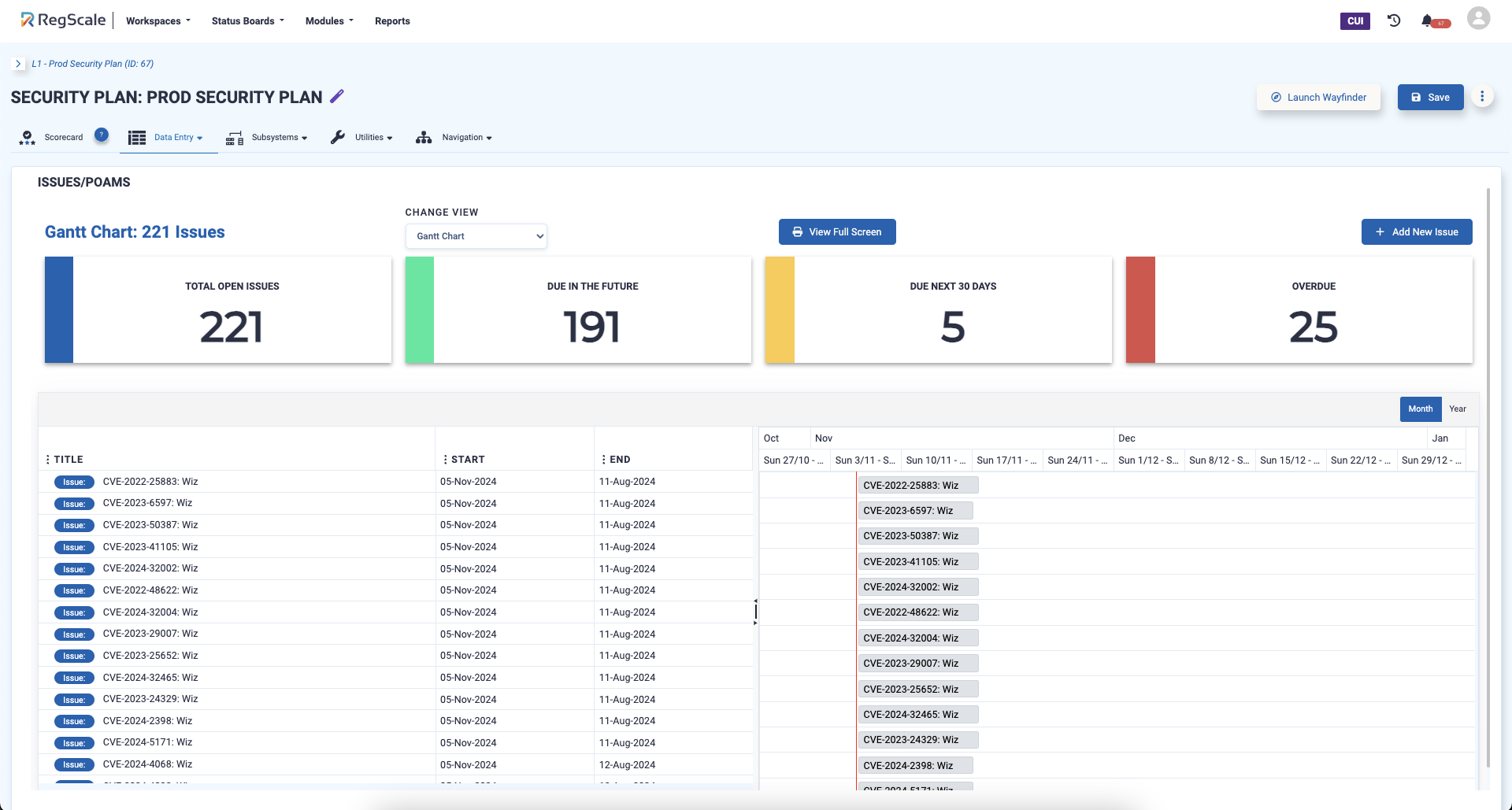
Closing the Loop on Compliance
With the RegScale platform, open tickets are continuously updated as code is fixed and patching is completed. A rescan occurs either manually or through an automated or scheduled scan, and the new scan result is then fed back to RegScale to update and track the status. The platform can also initiate escalations based on SLAs that are not being met.
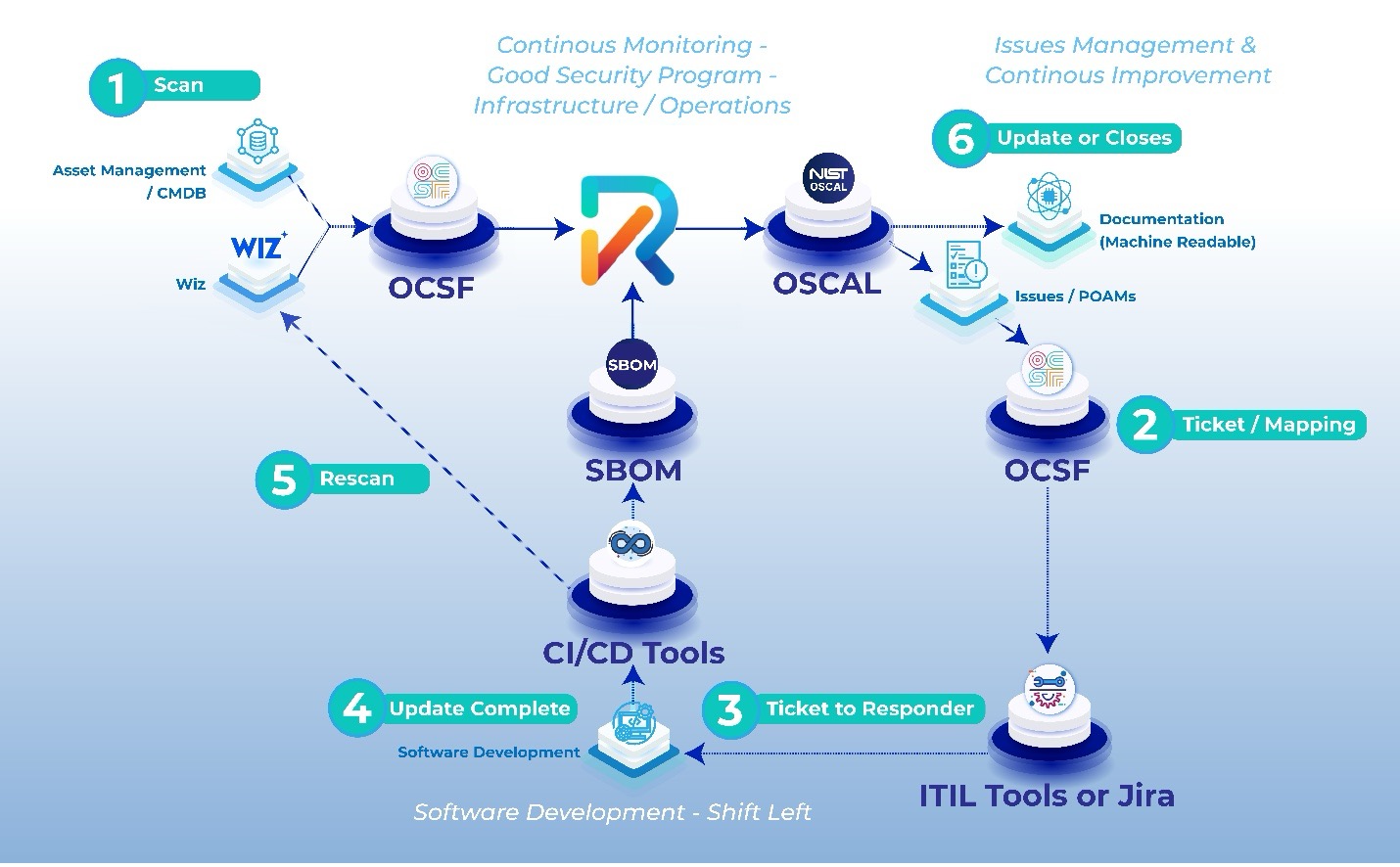
For FedRAMP customers, POAMs and all other documentation can be exported in the requested format (such as OSCAL, Word, or Excel) along with the SSP in order to adhere to continuous monitoring requirements.
RegScale + Wiz: Enhancing Security, Risk, and Compliance
With a torrent of vulnerability data flooding into the SOC, it’s become increasingly difficult to understand the risk and business impact of each new vulnerability. RegScale’s platform takes the Wiz scan information and contextualizes it, giving you a clear, concise view of the risks associated with each asset and vulnerability. This enables you to properly prioritize resources to respond to the issues and minimize risk exposure.
To learn more about how Wiz and RegScale can support your cloud asset compliance and continuous cloud security, explore our resources or schedule a demo.
Ready to get started?
Choose the path that is right for you!
Skip the line
My organization doesn’t have GRC tools yet and I am ready to start automating my compliance with continuous monitoring pipelines now.
Supercharge
My organization already has legacy compliance software, but I want to automate many of the manual processes that feed it.