Streamline Your Governance, Risk, & Compliance
Streamline your governance, risk, and compliance processes with shift-left security and compliance as code. RegScale’s Continuous Controls Monitoring (CCM) platform delivers constant audit-readiness and continuously self-updating paperwork. Designed as a cloud-native solution, RegScale also delivers hybrid and on-premises solutions so you can integrate compliance as code into your CI/CD pipelines, speed certification, reduce costs, and future-proof your security posture.
Trusted by the most secure and compliant organizations on the planet

RegScale Named a Cool Vendor in the 2025 Gartner® Cool Vendors™ with AI-Powered Technologies for Assurance Leaders
This recognition highlights our AI-driven Continuous Controls Monitoring platform that transforms compliance into a continuous, automated process — helping enterprises stay audit-ready, reduce risk, and move faster.
AI- and Automation-Driven Success
Whether you’re just starting on your compliance journey or adding a new framework to an existing program, RegScale helps you mature your security, risk, and compliance posture. Integrate compliance as code to generate outsized ROI and rapid time-to-value with only 20% of the time and money of legacy GRC tools.


FedRAMP Certification
Get FedRAMP High 3-4x faster than average using AI-driven workflows for automated generation of artifacts and compliance as code with NIST OSCAL.
Learn More


Rapid Certification
Wizard-driven and guided processes to rapidly obtain certifications with 60+ natively supported regulations, including NIST 800-53, FedRAMP, CRI, PCI DSS, CMMC, NYDFS, SEC, FFIEC, DORA, and more.
Learn More


Automated Evidence Collection
Integrations with leading scanners, cloud hyper-scalers, DevSecOps, and ITIL tools to provide seamless automation for evidence collection and intelligent remediation workflows.
Learn More


Simplified Risk Management
Consolidated and actionable roll-up reporting for audit risk, third-party vendor risk, threat-modeling and system risk, and enterprise risk management processes.
Learn More


DevSecOps Continuous Compliance Automation & Compliance as Code
Shift-left security with compliance as code integrated into your CI/CD pipelines to speed certification, reduce costs, and improve your security posture from the first line of code through deployment.
Learn More


Continuous Controls Mapping
Implement and assess once, then reuse across multiple frameworks to eliminate redundant work and enter new markets more rapidly.
Learn More
Knock down silos and consolidate your controls library
REGULATIONS
Manage and assess controls across multiple compliance frameworks, leveraging advanced AI and automation to stay ahead of the changing regulatory landscape.
POLICIES
Create and manage controls for policies and procedures with your internal policy documents and our advanced AI.
RISKS
Gain visibility and manage controls to understand and mitigate risks across your environment.
Automated controls lifecycle management
Simplify and streamline your control lifecycle with advanced automation, industry-leading AI, and pre-built business processes based on decades of lessons learned in the industry. Rapidly configure to meet your unique business requirements and then ruthlessly automate every phase of the control lifecycle.

01: Build the Program
60+ natively supported regulations, including NIST 800-53, FedRAMP, CRI, SOC2, SOX, PCI DSS, CMMC, NYDFS, SEC, DORA, FFIEC, and more.
Implement and assess once, then reuse across multiple frameworks to eliminate redundant work and enter new markets more rapidly.
Build your program with intuitive and guided workflows that lead you step-by-step to ensure consistent execution.
Leverage advanced AI to explain controls, author them, evaluate them, and get expert advice on how to improve their quality and completeness.
02: Collect the Evidence
Manage a centralized evidence repository with advanced automation to stay always audit-ready. Say goodbye to waiting on others to collect and send evidence; keep evidence always up-to-date and at your fingertips.
Understand in detail the changes to your security, risk, and compliance posture over time. Our patented Time Travel system allows you to view every change to every record over its lifecycle to understand and document how changes improve security and compliance and reduce risk.
Extend our platform to integrate with any technology or security stack using our 1300+ APIs, native OSCAL and OCSF support, and Security Graph.
Integrate with industry-leading security scanners, cloud hyper-scalers, ITIL tools, and DevSecOps tooling. Just turn it on, set it, and let RegScale’s automation engine do the rest.
03: Assess the Controls
Not every control can be automated. We’ve built the simplest and fastest solution in the market for conducting manual control assessments.
Nobody wants to give auditors unfettered access to their system of record. We auto-generate artifacts in Microsoft Office so you can stay always audit-ready and provide point-in-time snapshots on demand.
Integrate with industry-leading security scanners, cloud hyper-scalers, ITIL tools, and DevSecOps tooling. Just turn it on, set it, and let RegScale’s automation engine do the rest.
RegScale’s advanced AI reads policy documents and converts them to control statements in security plans. If you already have controls, RegScale’s AI can evaluate your control statements for accuracy and effectiveness, giving in-line suggestions for improving them. Take the control drafting process from weeks of work to minutes of review.
04: Fix the Issues
Tired of painful handoffs between IT and security? Sick of manual copy-and-paste exercises between tools? We automate and monitor remediation workflows end-to-end among the industry-leading commercial scanners and ITIL tools for more painless, effortless processes.
Need stronger governance in your remediation program? Customize our phase gate approval process to ensure that issues are fully remediated and verified and that they won’t recur.
No more surprises. Visualize your progress in completing your preventive and corrective actions and ensure you stay on top of deadlines and deliverables. Visualize and manage remediation progress effectively, staying organized and meeting deadlines with ease. Leverage AI-enhanced analytics to prioritize tasks and allocate resources efficiently, ensuring timely resolution of issues and maintaining compliance with regulatory requirements.
Automate communication between security, development, and IT systems to enhance transparency, reduce risk, and minimize attack surfaces and response times. Ensure seamless end-to-end vulnerability management, accelerate mean time to remediation, provide full audit traceability, and maintain up-to-date evidence and documentation. Utilize AI algorithms to detect and prioritize vulnerabilities, enabling proactive risk mitigation and ensuring continuous compliance with cybersecurity standards such as PCI and FedRAMP.
05: Manage the Risk
Controls are most effective when they are aligned to actual attack scenarios. Our threat modeling solution allows you to build risk mitigation programs based on how your systems will actually be attacked.
Our Enterprise Risk solution expands beyond IT/cyber risk into advanced risk modeling for your full range of organizational needs, including HR, legal, safety, and more.
Focus risk management practices at the lowest level possible with a 360-degree view of assets, and prioritize based on information types, misconfigurations, and vulnerability data. Assess the risk of non-compliance with regulatory frameworks, provide mitigating controls, and document and approve exceptions.
Automated Impact Assessments produced with AI-driven insights provide contextual projections of potential outcomes and costs — enabling you to align your business decisions with your organizational goals while staying within your defined risk tolerances.
Flow down requirements to vendors and ensure compliance with our advanced questionnaire system, procurement system integrations, and automated assessment capabilities.
Translate risks to dollars using our quantitative risk analysis tools with Monte Carlo simulations that help translate risk mitigation plans to bottom-line ROI.
06: Govern the Risk
Out-of-the-box and fully customizable reports, dashboards, and scorecards help you visualize your compliance and risk posture in real-time. Extend to BI tools using Graph and APIs.
Provide real-time integrations with broader organizational business tools and processes using our real-time, event-driven architecture and advanced workflow automation.
Sometimes there’s no way around it; you have to deviate from policy. Our exception management process allows you to document the potential risk, establish durations for the exception, and ensure strong governance that remains transparent across the organization.
Maintaining your risk and compliance posture over time takes discipline. Our change management process documents every difference, so you are always audit ready.
Never get surprised in an audit again. Our real-time alerts integrate with Teams, Slack, and email to ensure your employees get notified in real-time as issues arise.
Extreme automation, advanced AI, and actionable data
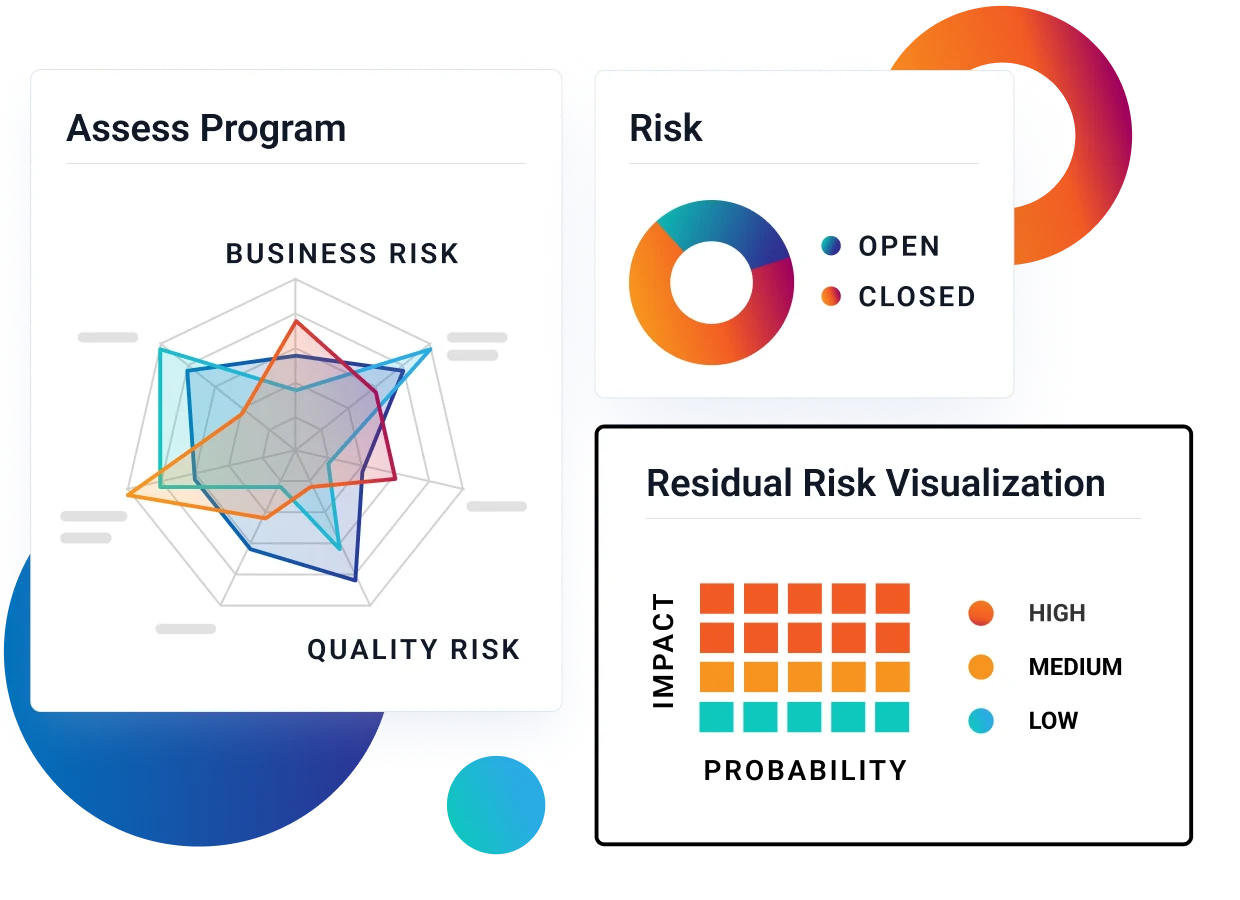
Break down data silos
Stop chasing evidence to assemble, validate, and give to auditors. RegScale continuously collects all your risk and compliance data in one place, generates self-updating paperwork, and makes information readily accessible to any user or system that needs it.
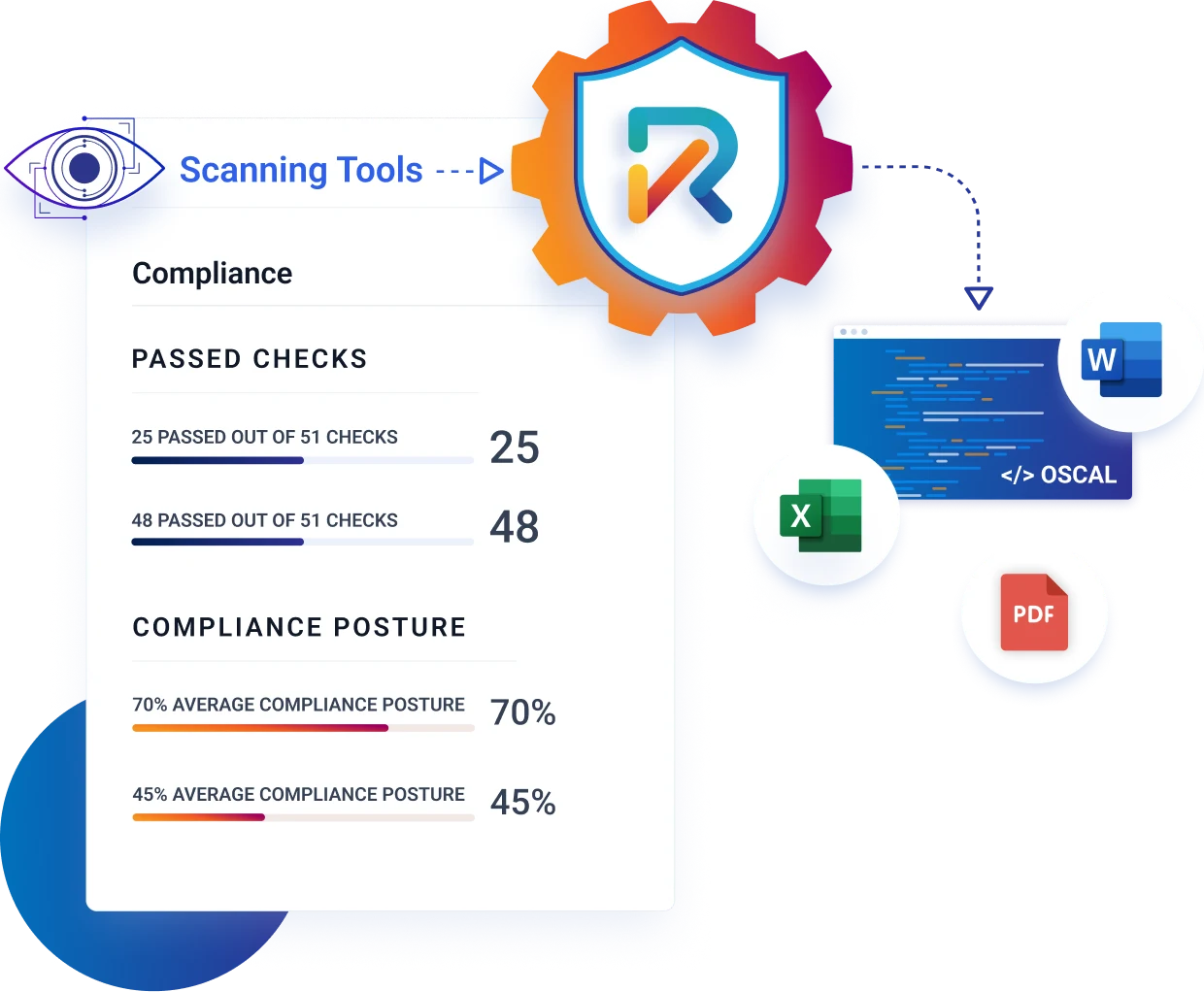
Unleash extreme automation
Manual copy-and-paste exercises are both soul-crushing and error-prone in the risk and compliance arena. Use our advanced automation platform to streamline your workflows and self-generate compliance artifacts in OSCAL, Word, and Excel on demand. Real-time customized dashboards give you full visibility into your security, risk, and compliance status.

Unlock AI everywhere
The GRC industry exists to provide paperwork nobody wants to read, and nobody wants to write. RegScale’s AI companion writes your controls, conducts your audits, and tells you where you can make improvements for the greatest impact. Our compliance AI not only saves you time but also fills in staff skill gaps, letting you focus on the most important parts of the business.
Ready to get started?
Choose the path that’s right for you!
Start Your Journey
My organization doesn’t have GRC tools yet. I need to get out of spreadsheets and start automating my continuous monitoring and GRC program.
Supercharge
My organization already has legacy compliance software, but I want to automate many of our manual processes, gain better visibility into our organizational risk, and fill in gaps in skills and knowledge as we expand into new markets.
































