Mesh Architecture and Compliance Automation Boost Security
Seamlessly plug and play our continuous controls monitoring (CCM) platform into your organization’s security stack. By integrating data from across your organization, RegScale enables you to continuously automate risk assessments and compliance workflows, generate self-updating paperwork, and enable compliance as code to replace manual processes and add real-time visibility into all compliance and security procedures.
Trusted by the most effortlessly secure and compliant organizations on the planet
The power of RegScale CCM
Easily add automations to all your compliance workflows
CCM is a modern mesh architecture for governance, risk, and compliance that helps you become the lords of automation. Simplifying audit prep is just the tip of the iceberg. This framework also solves many advanced security challenges by uniting multiple data sources so they can be centrally analyzed. Use our built-in AI to find all your data and workflows, our APIs to integrate them, compliance-as-code to bind them, and RegScale to manage it all.
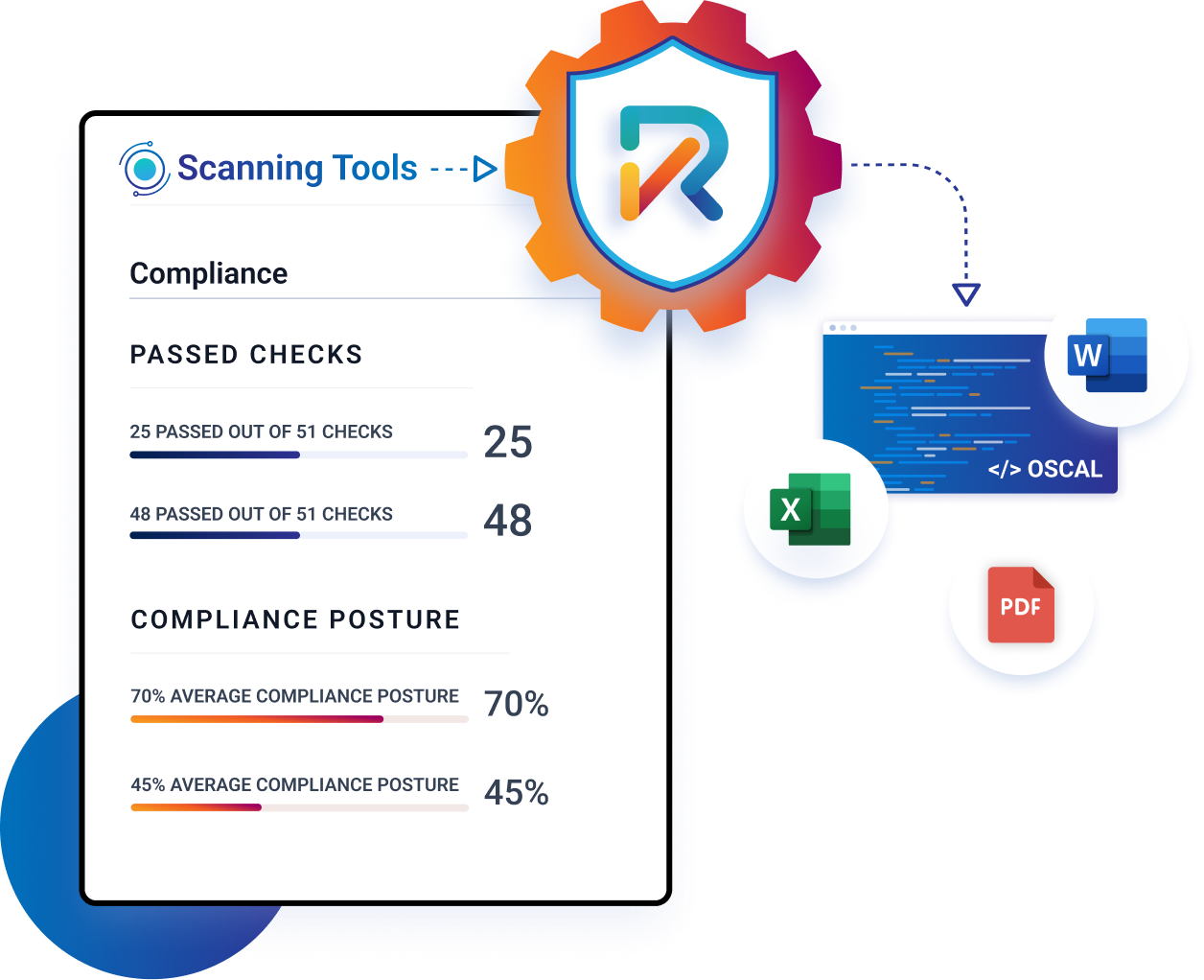
Compliance-As-Code Automates Documentation
RegScale is built using NIST OSCAL formats, generating the documents you need for compliance in machine-readable formats. By replacing manual processes, compliance-as-code enables you to futureproof your FedRAMP program, build more precise AI models to train on your data, and build a foundation for automation of security and compliance checks.
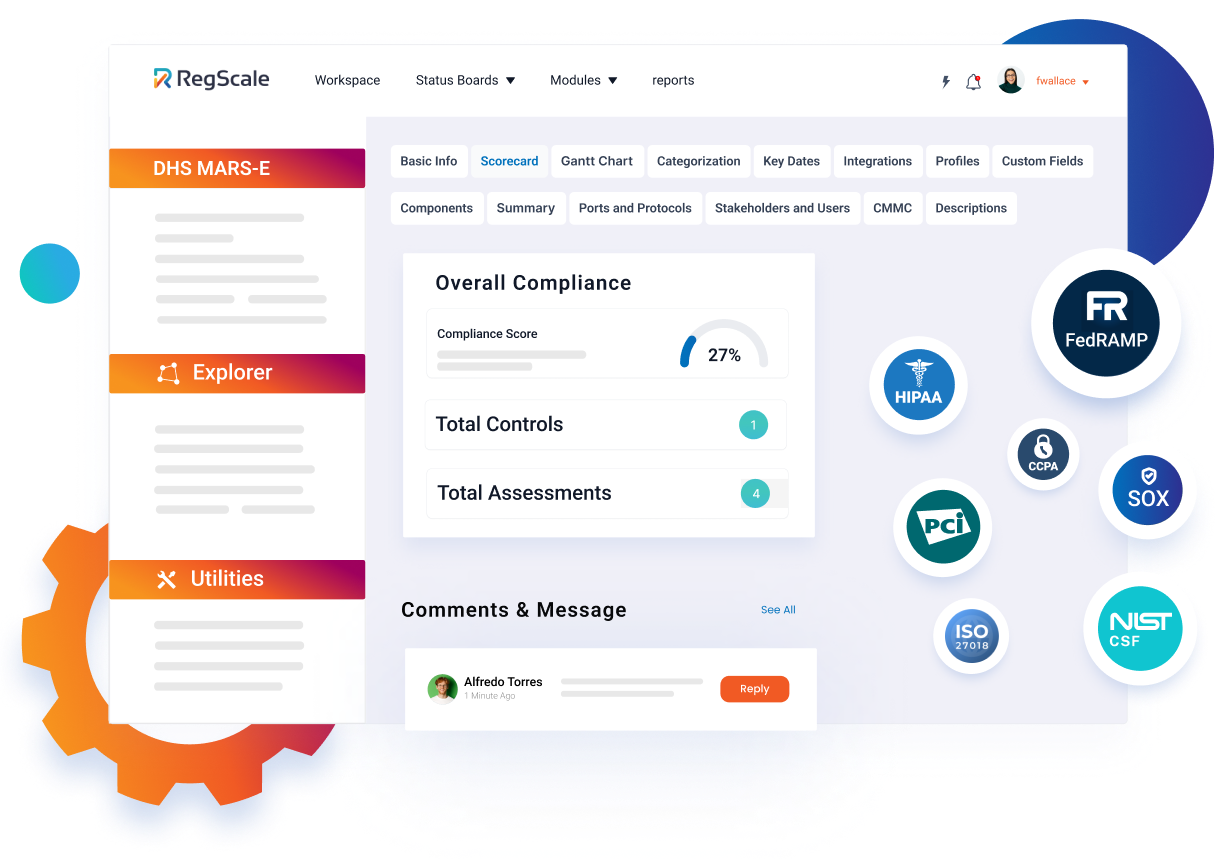
Integrations for Real-Time Self-Assessments
RegScale’s compliance automation platform integrates with more than 40 industry-leading tools, including ITIL ticketing systems and vulnerability scanners. This enables your tools to conduct self-assessments of your controls and log issues in real-time.

See what RegScale can streamline for you
Book a demo now for a quick walkthrough of how our continuous controls monitoring can solve your compliance, risk, and cybersecurity challenges.
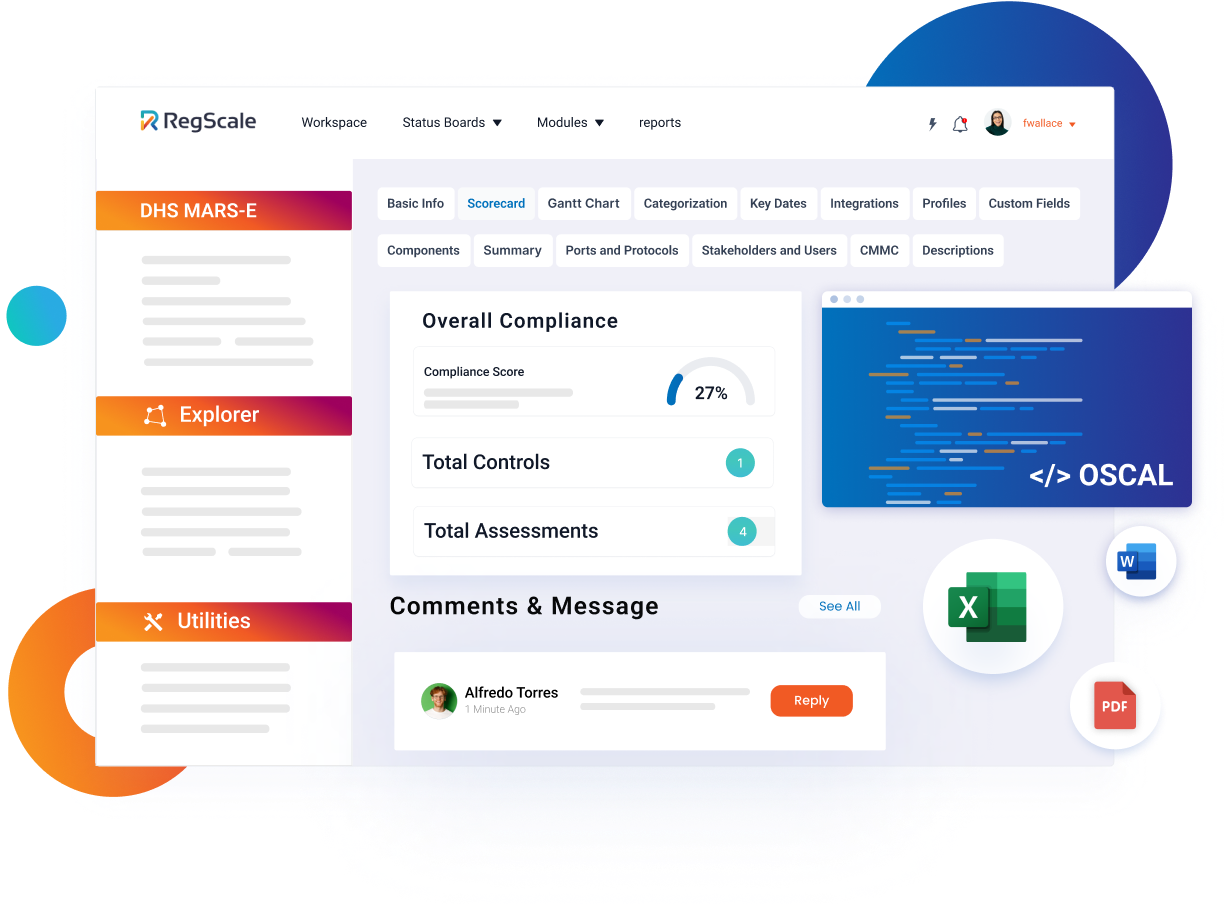
APIs and Graph Enable Seamless Data Exchange
RegScale enables your compliance systems to interoperate seamlessly, with more than 1,300 APIs and a GraphQL (build your own API) architecture that allows for seamless data exchange between systems.
Microsoft Office Automation
RegScale’s self-updating paperwork automations even include the ability to auto-generate your documents into Microsoft Word and Excel formats, just as your regulators, Board of Directors, or other stakeholders would expect.
Automate Controls Lifecycle Management
Simplify and streamline your controls lifecycle with advanced automation, industry-leading AI, and pre-built business processes based on decades of lessons learned in the industry. Rapidly configure to meet your unique business requirements and then ruthlessly automate every phase of the controls lifecycle.

01: Build the Program
1000+ Supported Regulations, including NIST 800-53, FedRAMP, SOC2, SOX, PCI DSS, NYDFS, SEC, DORA, FFIEC, and more!
Implement and assess once, then reuse across multiple frameworks to eliminate redundant work and enter new markets more rapidly.
Intuitive and guided experiences to build the program using dynamic wizards that ensure consistent process execution.
Leverage AI to explain controls, author them, and perform automated edits to reduce or eliminate many manual labor tasks.
02: Collect the Evidence
Say goodbye to data calls from regulators and Internal Audit. Manage a centralized evidence repository with automation and become always audit ready.
Understand in detail the changes to your risk and compliance posture over time. Our patented Time Travel system allows you to view every change to every record over its lifecycle.
World's first headless CCM platform. Extend our platform to integrate with any technology or security stack using our 1200+ APIs and Security Graph.
Dozens of integrations with the leading security scanners, cloud hyper-scalers, ITIL tools, GRCs, and DevSecOps tooling. Just turn it on, set it, and forget it.
03: Assess the Controls
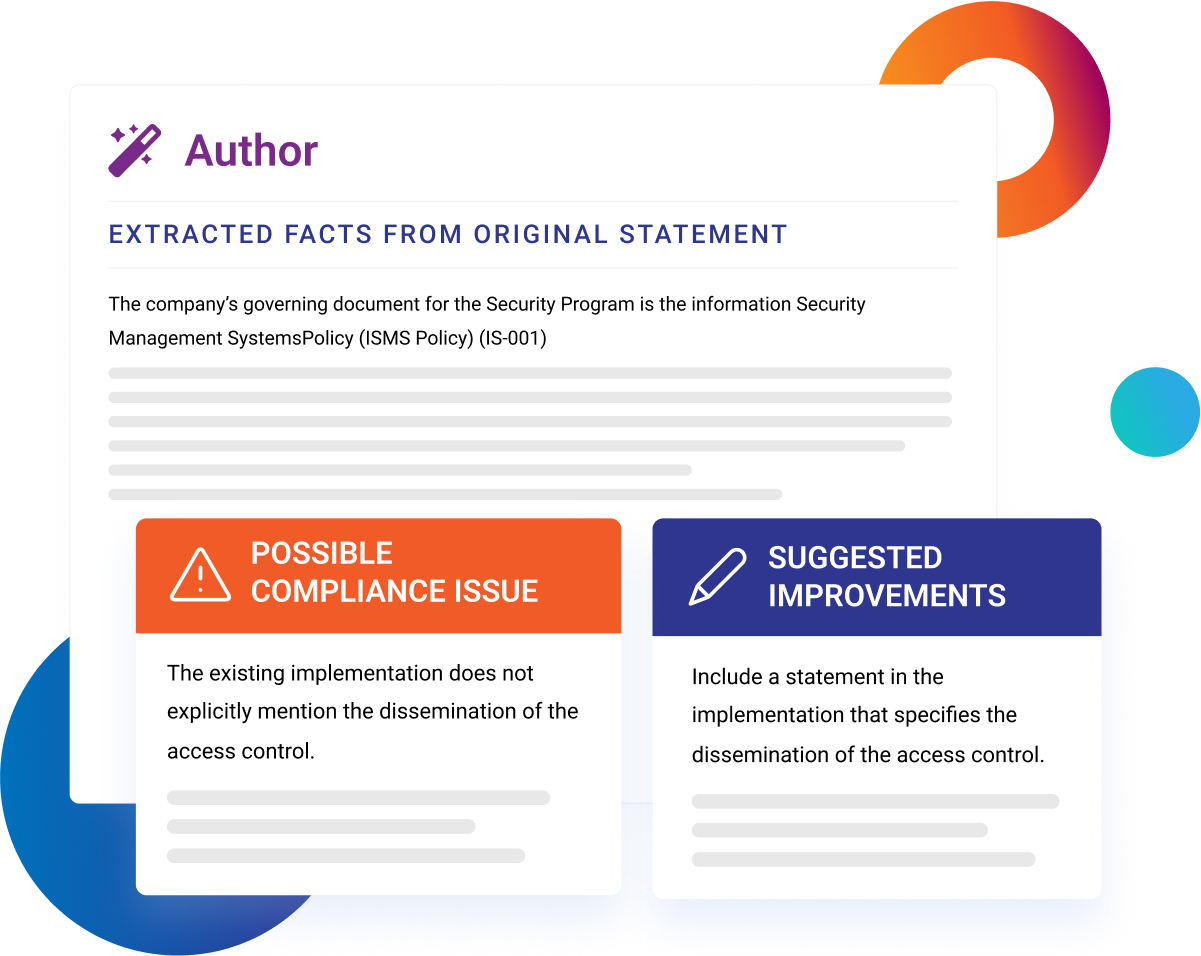
Not every control can be automated. We have built the simplest and fastest solution in the market for conducting manual control assessments.
Nobody wants to give auditors access to their system of record. We auto-generate artifacts in Microsoft Office on demand, so you are always audit-ready and can provide point-in-time snapshots at any time.
Dozens of integrations with the leading security scanners, cloud hyper-scalers, ITIL tools, GRCs, and DevSecOps tooling. Just turn it on, set it, and forget it for automated technical assessments.
Tired of reading lengthy and boring security program documentation in Word and Excel? Let our AI auditor take the first pass and perform automated compliance audits in minutes.
04: Fix the Issues
Tired of painful handoffs between IT and Security and manual copy-and-paste exercises between tools? We automate remediation workflows end to end between the leading commercial scanners and ITIL tools.
Need stronger governance in your remediation program? Customize our phase gate approval process to ensure issues are fully remediated and verified and that they won't reoccur.
Visualize progress in completing your preventive and corrective actions and ensure you stay on top of deadlines and deliverables.
Accelerate mean time to remediation of vulnerabilities while providing full audit traceability using our comprehensive vulnerability management workflows.
05: Manage the Risk
Controls are most effective when they are aligned to actual attack scenarios. Our threat modeling solution allows you to build risk mitigation programs based on how your systems will actually be attacked.
Our Enterprise Risk solution expands beyond IT/Cyber risk into advanced risk modeling for the full range of organizational needs (HR, Legal, Safety, etc.).
Focus risk management practices at the lowest level possible with a 360-degree view of assets. Prioritize risk management based on information types, misconfigurations, and vulnerability data.
Flow down requirements to vendors and ensure compliance with our advanced questionnaire system, procurement system integrations, and assessment capabilities.
Assess the risk of non-compliance with regulatory frameworks, provide mitigating controls, and document and approve exceptions.
Translate risks to dollars using our quantitative risk analysis tools with Monte Carlo simulations that help translate risk mitigation plans to bottom-line ROI.
06: Govern the Risk
Out-of-the-box reporting, dashboards, and scorecards visualize compliance and risk posture in real-time. Extend to BI tools using Graph and APIs.
Compliance and risk processes do not execute in isolation. Provide real-time integrations to broader organizational business processes using our real-time, event-driven architecture.
Nobody is perfect and sometimes you have to deviate from policy. Our exception management process allows you to document the risk, establish durations for the exception, and ensure strong governance.
Maintaining your risk and compliance posture over time takes discipline. Our change management process documents every difference so you are always audit ready.
Never get surprised in an audit again. Our real-time alerts integrate with Teams, Slack, and email to ensure your employees get notified in real-time as things change and deliverables are due.
Ready to fast track your compliance? Let us show you how it’s done
Hey, we know reading can only get you so far. That’s why we’d like to give you a quick, live walk-through of RegScale, to show you exactly what we can do for your organization.








