Unified Cybersecurity Language: Optimizing Risk and Compliance Terms for Collaborative Security

Kickoff: Navigating the Cybersecurity Language Landscape
Imagine the chaos when a cybersecurity breach puts data at risk, and departments are left in a scramble. Cybersecurity tags the event a ‘security incident,’ Risk counters with a ‘data breach,’ while Compliance cries out ‘SLA violation’. The jargon jumble does more than confuse – it hampers the swift and decisive action needed when every second counts to protect data.
Are your teams in harmony, or is your cybersecurity choir out of tune? In today’s ever evolving and increasingly complex world, clear and consistent internal communication isn’t just advantageous – it’s the cornerstone of organizational resilience to the threats of today and beyond. Dive into the undeniable power of syncing the lingo across your security, risk, and compliance teams and the technology they trust.
Decoding the Dilemma: The Cost of Misaligned Security Terms
Navigating among the maze of corporate communication, organizations face a formidable foe: the discord of conflicting terms echoed by their array of tools, systems, and teams. Misaligned terminology spans several adversaries:
- Fog of Inefficiency – When tools become estranged from an organization’s linguistic map, they generate steep learning curves for adoption, operation, and reporting. Misunderstandings proliferate, clouding data interpretation like fog over a battlefield, where clarity is the key to victory.
- Specter of Risk – A symphony of dissonant security terms become a siren song for vulnerabilities, carving paths for threats to slip through the cracks unnoticed, much like shadows slipping past in the night.
- Anchor of Hesitation – With every team echoing a different call for the same threat, precious time dribbles away in the pursuit of consensus. In the swift currents of today’s digital wave, hesitation is the anchor dragging down the ship of decisions and progress.
Tales from the Trenches – How Muddled Terminology Muddies the Cyber Waters
In a healthcare organization, the terms ‘Plan of Actions and Milestones (POA&M)’ and ‘remediation plan’ were used interchangeably between the compliance and security teams. This led to a situation where the compliance team was waiting for a POA&M to address regulatory findings, while the security team was actively working on a remediation plan for identified vulnerabilities, thinking they had fulfilled their obligation. The overlap caused a delay in meeting regulatory requirements and increased the window of risk before vulnerabilities were properly mitigated.
A financial services company experienced unauthorized access to its database. The security team referred to it as a ‘security incident’, initiating a standard protocol that did not prioritize immediate external communication. The risk management team, however, labeled it a ‘data breach’ and was prepared to notify customers and regulators, considering potential data exposure. The compliance department was on standby to report an ‘SLA violation’ due to interrupted services. The lack of unified terminology delayed the coordinated response and led to a regulatory fine for late customer notification of a ‘breach.’
Code of Clarity: Implementing Custom System Labels for Precision
Enter Custom System Labels: not just a feature, but a keystone in the archway of cyber communication. By aligning the nomenclature within your tools – like renaming ‘supply chain’ to ‘third party risk management’ – these labels go beyond mere semantics. They act as a beacon, guiding all departments to a unified understanding. This tailoring extends into the very fabric of your platform, allowing for a seamless match with your organization’s taxonomy, whether it be modules, objects, fields, or terminologies.
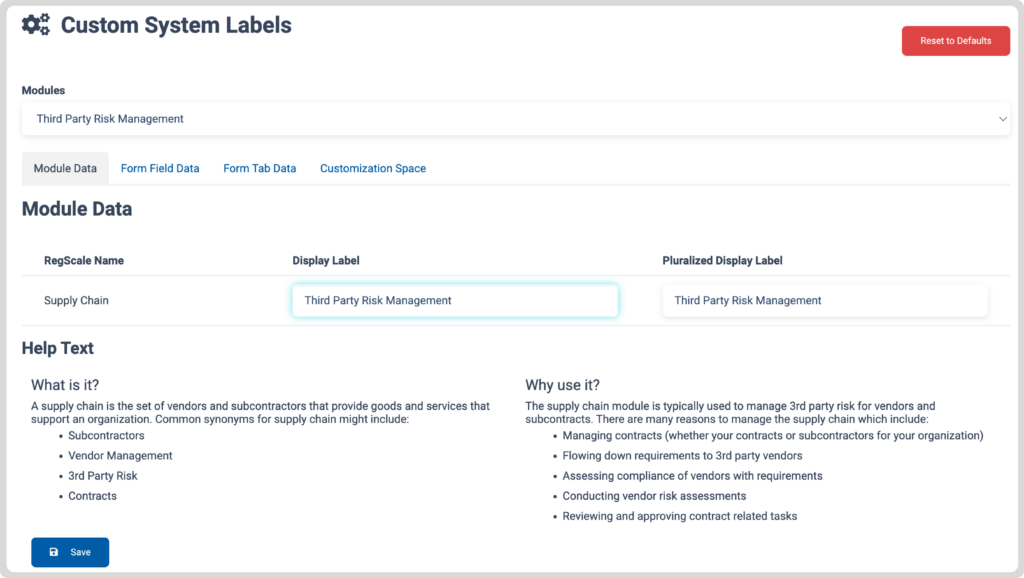
Custom System Labels – Supply Chain to Third Party Risk Management
Unlocking Synergy: The Compelling Advantages of Standardized Security Speak
Strategic labeling of terms within your cybersecurity toolbox eradicates the haze of ambiguity. It avoids the guesswork, and even more, it orchestrates a symphony of departmental expertise into a harmonious narrative of security, risk, and compliance. Such clarity in communication not only expedites decision-making but also instills robust confidence in those decisions, resonating through every layer of the organization. The ripple effects — a fortified defense line streamlined risk management, and a compliance posture so resilient it becomes a benchmark. Embrace this linguistic unity and watch as it translates into operational excellence and an improved bottom line.
Your Cyber Glossary Blueprint: Strategies for Unified Communication
Transform your team’s communication efficiency with these tactical maneuvers:
- Build a Unified Command Language
Erect the foundation of interdepartmental dialogue with custom system labels. Picture your teams, once divided by jargon, now marching in tune, guided by shared language that bridges security, risk, and compliance disciplines. - Assemble Your Linguistic Map
Draft the definitive ‘Linguistic Map’ of your cybersecurity realm – a taxonomy guide that acts as a ‘Rosetta Stone’ for deciphering internal dialogue. It’s not just a guide; it’s the key to unearthing the context behind every term for current and future cybersecurity crusaders. - Audit Your Technological Linguists
Conduct a review of your digital tools to ensure they ‘speak’ and ‘understand’ your organization’s cybersecurity taxonomy. Upgrade your technological translators where they fall short, reinforcing the infrastructure of your cyber communications. - Demand Linguistic Compatibility in New Tech
When enlisting new tools in the cyber armory, insist on custom label capability. It’s a safeguard, ensuring that each new gadget adds strength to your defenses and resonates with your established communication protocols for tools and team.
In the interconnected and swiftly changing landscape of business tech, a unified cybersecurity language is not just beneficial – it’s your shield and sword. RegScale’s continuous controls monitoring platform is your ally, shattering the chains of legacy GRC limitations with features like custom system labels – tailored to the unique dialect of your digital dominion.
Embrace RegScale’s arsenal and witness how a shared language can not only fortify your cyber defenses but also oil the gears of risk management and compliance efficiency. This isn’t just progress – it’s a revolution navigated by the power of understanding.
Don’t let your cybersecurity efforts be muffled by a cacophony of technical tongues. Are you poised to synchronize your cyber lingo with the pulse of organizational success?
Take the first step: Contact RegScale today for a personalized demonstration.
Ready to get started?
Choose the path that is right for you!
Skip the line
My organization doesn’t have GRC tools yet and I am ready to start automating my compliance with continuous monitoring pipelines now.
Supercharge
My organization already has legacy compliance software, but I want to automate many of the manual processes that feed it.