In the world of FedRAMP authorization, a common stumbling block is the complexity and volume of security controls that organizations must implement and continuously monitor. But a more recent FedRAMP 20x development, the Key Security Indicators (KSI), is emerging as a powerful alternative that can improve operational insight and streamline the path to authorization.
This post explores all things KSIs: their origins and benefits, how they differ from controls, and how they’re reshaping the FedRAMP landscape for modern organizations. It also explains how RegScale developed an end-to-end prototype for automating the KSIs within our platform — and used it to achieve FedRAMP 20x results in under 90 minutes.
What Are Security Controls?
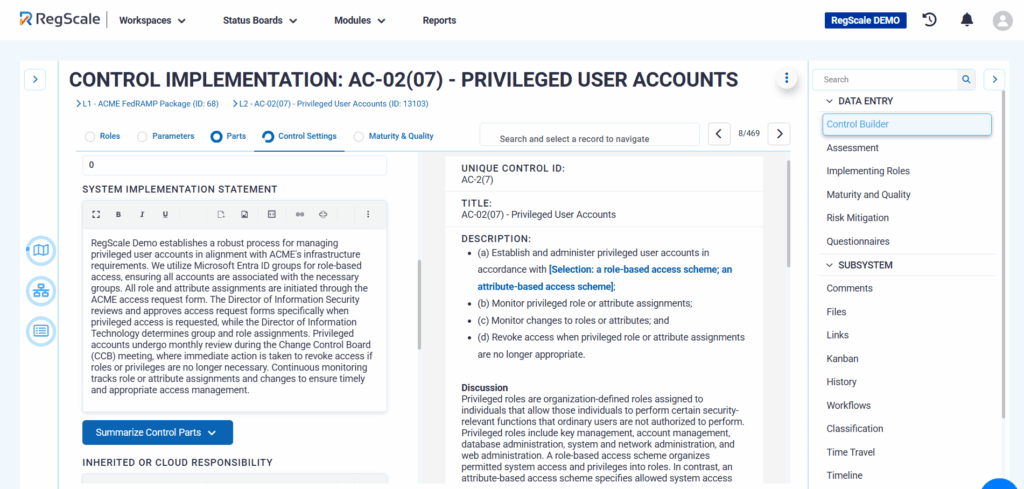
In FedRAMP (the Federal Risk and Authorization Management Program), security controls are prescriptive requirements based on NIST SP 800-53. These controls outline the measures an organization must implement to secure its systems and data, encompassing areas such as access controls, audit logging, incident response, and system integrity.
FedRAMP High baselines include 421 specific controls. These controls form the foundation of the Security Assessment Framework (SAF), and compliance requires rigorous documentation, implementation, testing, and ongoing evidence collection.
AI Generated Control Statement
What Are Key Security Indicators (KSIs)?
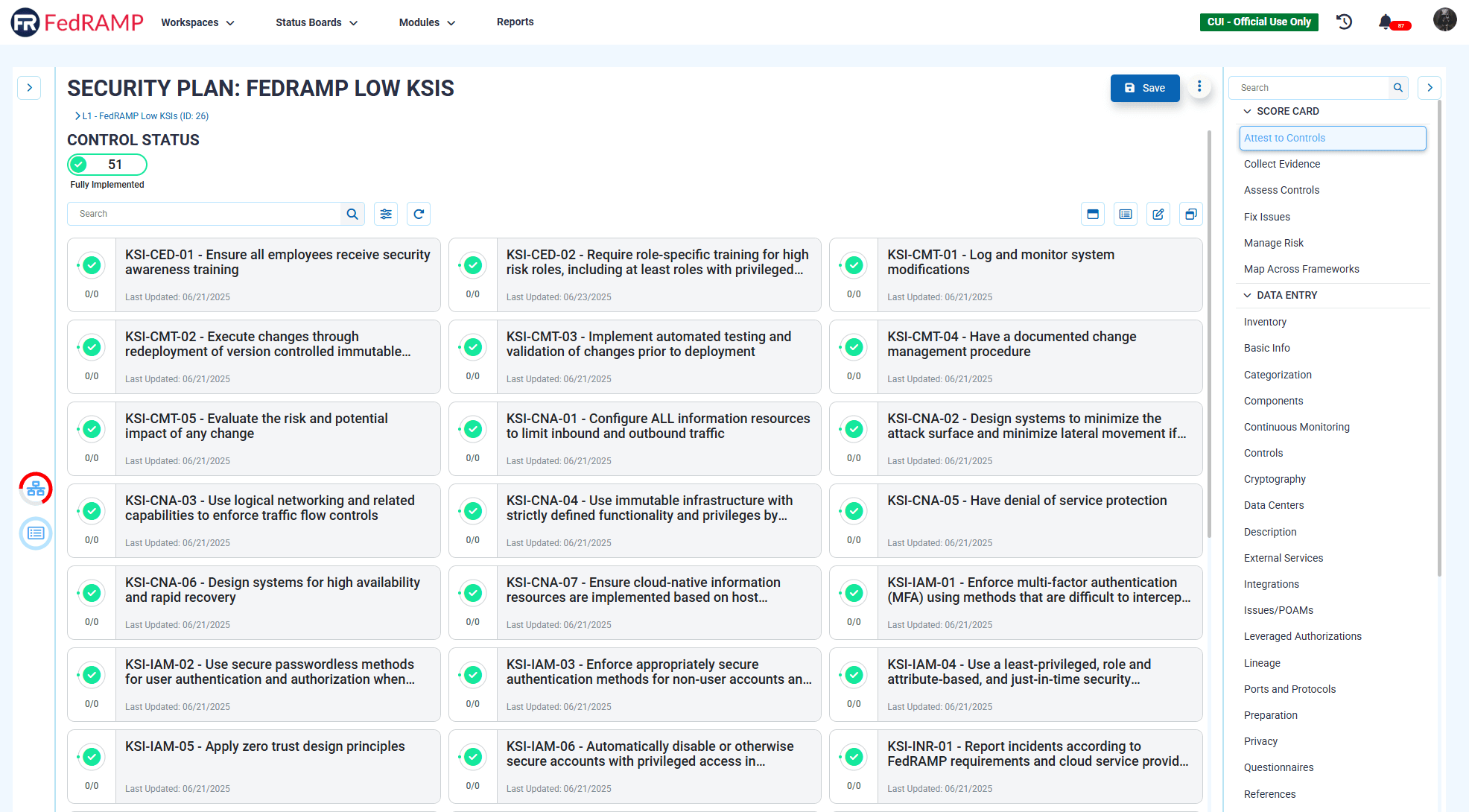
Key Security Indicators are quantitative, automated metrics that reflect the current state of a system’s security posture. Unlike controls, which tend to be binary and static (either “implemented” or “not implemented”), KSIs are continuous, real-time indicators of risk and compliance performance.
Manage KSIs just like controls in RegScale
KSIs evolved from the Continuous Diagnostics and Mitigation (CDM) program and Continuous Controls Monitoring (CCM) methodologies promoted by NIST and Department of Homeland Security (DHS). The idea is to focus on observable, automated signals that indicate whether security outcomes are being achieved, not just whether controls are in place. This focus on achieving security outcomes is one of the driving forces behind the FedRAMP 20x program.
Examples of KSIs include:
- Centrally track and prioritize the mitigation and/or remediation of identified vulnerabilities
- Enforce multi-factor (MFA) using methods that are difficult to intercept or impersonate (phishing-resistant MFA) for all user authentication
- Regularly review audit logs
- Have policies outlining the security objectives of all information resources
KSIs vs. Controls: Key Differences
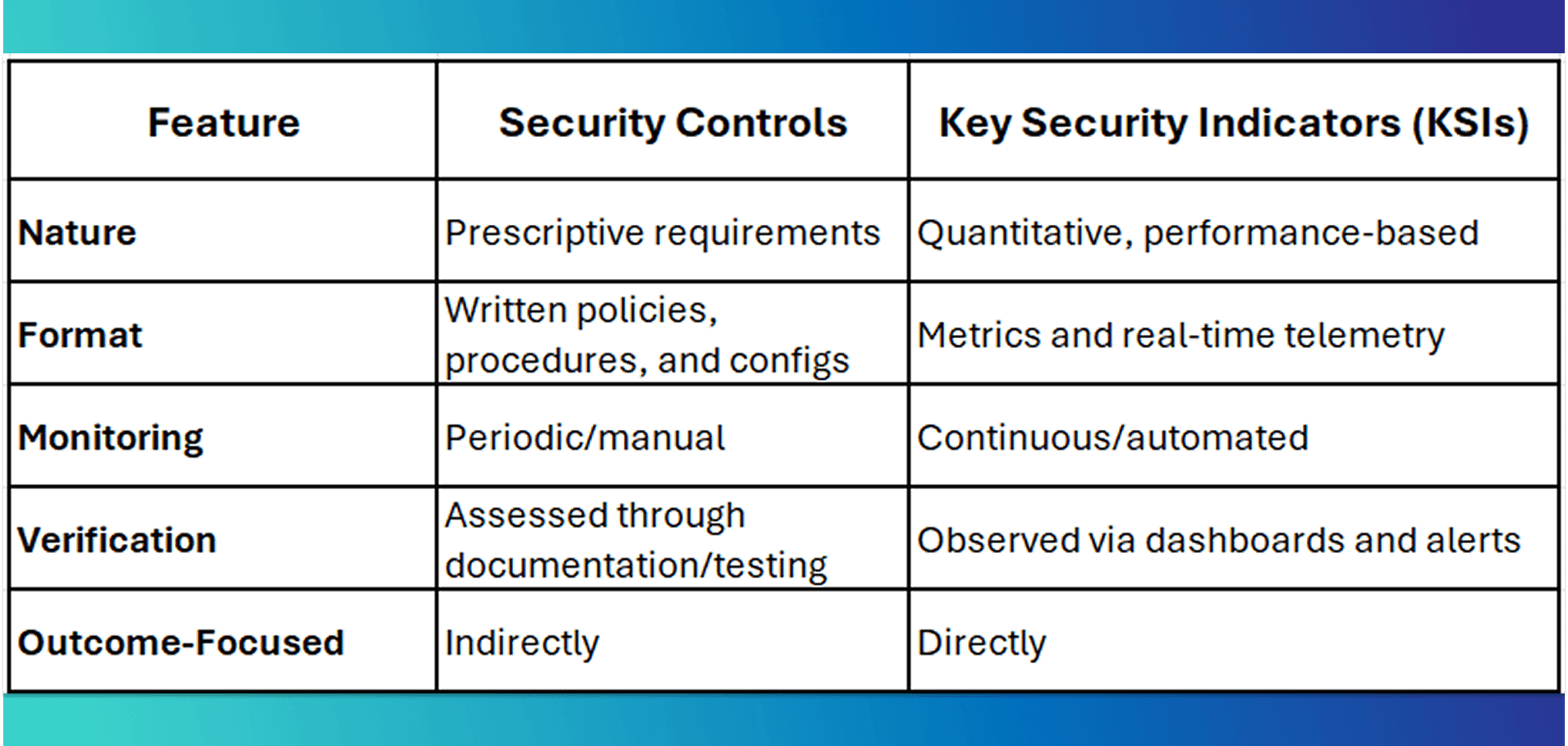
Comparing Traditional Controls to KSIs
Benefits of KSIs over Controls
Shifting to using KSIs for FedRAMP authorization offers several benefits for organizations looking to streamline their compliance programs.
- Real-Time Visibility
KSIs provide live insights into whether security objectives are being met, versus static snapshots during audits. - Operational Relevance
KSIs align with the tools and telemetry security teams already use, reducing redundant documentation. - Simplified Audits
Dashboards and automated reports make it easier to demonstrate compliance without lengthy policy reviews. - Improved Risk Management
KSIs focus on measurable outcomes that directly affect security posture, offering more value to CISOs. - Lower Compliance Overhead
Less time spent writing and updating control descriptions means more focus on improving security.
Why Controls Still Matter
Despite their drawbacks, security controls still serve important purposes:
- Regulatory Alignment: FedRAMP’s core framework is still based on NIST 800-53 controls. You must still map KSIs back to these controls.
- Assurance Structure: Controls provide a standard language for assessors and auditors.
- Completeness: Some controls (e.g., governance, policy, training) can’t be easily represented as metrics or automated indicators.
Ultimately, KSIs don’t replace controls; they augment them. Think of KSIs as a more modern way to continuously monitor whether controls are working and adjust them as needed.
Lowering the Barriers to FedRAMP with KSIs
For startups, SMBs, and even larger enterprises, the paperwork burden of traditional controls is often the biggest barrier to FedRAMP certification. Without AI and automation, it can take many months to complete the manual documentation that FedRAMP requires. KSIs present a new path forward by:
- Enabling automation-first compliance
- Reducing reliance on compliance experts and consultants
- Making security evidence continuous and accessible to both auditors and engineers
- Supporting agile environments where systems change frequently
As the leading CCM platform, RegScale is leading the charge in using KSIs to bring FedRAMP within reach for more organizations. Recently, we developed an end-to-end prototype for automating the KSIs within our platform — and used it to achieve FedRAMP 20x results in under 90 minutes.
Final Thoughts
KSIs represent a fundamental shift in how we think about compliance, from checking boxes to measuring outcomes. They’re not a replacement for controls but a powerful enhancement that can simplify FedRAMP readiness and increase confidence in an organization’s security posture.
As FedRAMP and NIST evolve toward continuous authorization, expect KSIs to become increasingly central to how compliance is achieved, measured, and maintained — and expect other frameworks to start adopting this continuous monitoring philosophy. It’s a long-overdue evolution in both security and compliance that we’re excited to help spearhead.
Ready to get started?
Choose the path that is right for you!
Skip the line
My organization doesn’t have GRC tools yet and I am ready to start automating my compliance with continuous monitoring pipelines now.
Supercharge
My organization already has legacy compliance software, but I want to automate many of the manual processes that feed it.
